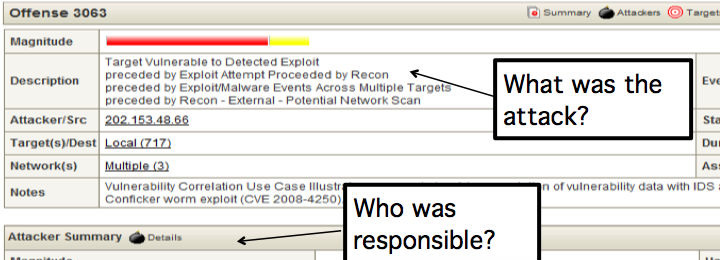
SIEM consolidates log source event data from thousands of devices endpoints and applications distributed throughout a network. It performs immediate normalization and correlation activities on raw data to distinguish real threats from false positives. As an option, this software supplies a list of potentially malicious IP addresses including malware hosts, spam sources and other threats. SIEM will also correlate system vulnerabilities with event and network data, helping to prioritize security incidents.
Why SIEM Management
Copyright © 2017 Cyber Security Africa. All Rights Reserved.